Jason Michael Milmont, of Cheyenne, Wyoming, may be only 19 years old, but he's already a very successful cybercriminal. In this Los Angeles FBI Press Release, Milmont confessed to controlling between 5,000 and 15,000 remote victims' computers, which he infected through modified versions of Limewire, and through Instant Message spam messages which lead users to infected websites. Links he placed on MySpace and PhotoBucket were also used to spread his malware.
In January, sources such as ComputerWorld were calling Nugache a challenger to the Storm Worm for its virility, and implied that hackers "tied to the Russian Business Network" may be responible for an upgraded version. Nugache was one of the first botnets to be controlled via a Peer to Peer or distributed interface. Lacking a central Command & Control made it more difficult to identify the real controller of the network.
Milmont confessed to being the programmer -- so, it was a 19 year old in Wyoming, rather than a Russian boogie man in this case. Using a graphical user interface Milmont created, he could easily harvest the stolen credentials which the Nugache worm was gathering from his victims as they logged in to their banking and credit card sites. Infected machines could be remotely upgraded to receive new versions of the malware. The third version added the key-logging software to the malware kit.
Although Milmont harvested many credentials, he is only being asked to pay $73,866.36 in restitution, for purchases made using the stolen credit cards. Milmont shipped packages to vacant addresses where he then picked the packages up himself.
Jason studied computers at Laramie County Community College in Cheyenne. One of his instructors there, Roger Findley, described him as extremely intelligent but socially awkward.
By pleading guilty, Milmont will only be charged with a single count of a violation of 1030 (a)(4), accessing a computer without authorization with intention to defraud and obtain a thing of value. The maximum sentence to that plea would be 5 years and a $250,000 fine.
View the 22 page plea agreement here.
Links:
http://www.theregister.co.uk/2008/06/28/nugache_creator_plea_agreement/
Monday, June 30, 2008
Saturday, June 14, 2008
Chinese Hackers hit Congress?
The early news from US Representative Frank Wolf (R-VA) came out on June 11th, when Wolf submitted House Resolution 1263, calling for the Sergeant at Arms of the House of Representatives to "ensure that all Members, committees, and offices of the House are alerted to the dangers of electronic attacks on the computers and information systems used in carrying out their official duties and are fully briefed on how to protect themselves, their official records, and their communications from electronic security breaches". This is what the news story should have been -- that Representative Wolf calls for tighter security. A news-worthy and noble action, which is long overdue and would receive wide support from the Security Community.
The single line from his Resolution which has captured all of the attention came from this "Whereas" . . .
More than 1100 news stories on Google mention the story, with some of the international mud-slinging using headlines like "US Accuses Chinese of Hacking Government Computers" which gained replies of "China says it's incapable of hacking Reps' computers".
Wolf didn't use such headlines -- the news story on his own website is headlined with Wolf Reveals House Computers Compromised by Outside Source. His office works with human rights activists and political dissidents around the world, and his emails and correspondence with some of these individuals was apparently compromised. He does say "My suspicion is that I was targeted by Chinese sources because of my long history of speaking out about China's abysmal human rights record." He also says that the Foreign Affairs Committee computers and that of other members who work "to help people who are suffering around the world" were similarly targeted.
That record is perhaps put most plainly in this impassioned speech by Representative Wolf from July 2007 -- Made in China, accuses China of poisoning toothpaste and toys, dumping products at below the cost of production on the international markets, arresting hundreds for religious beliefs and interring them in "slave labor camps", and compares their bid for the Olympics to that of the Nazis.
Wolf's words of warning on the Hill quote from several other sources as he issued his call for arms -- including a Congressional Research Service report indicating that 140 different foreign intelligence organizations regularly attempt to hack into the computer systems of US government agencies and US companies.
Joel Brenner, National Counterintelligence Executive of the Officer of the Director of National Intelligence used that figure in his speech here, and told CNN in October, it isn't just China, "there are about 140 foreign intelligence organizations trying to hack into the US government and US companies".
(Brenner also discussed the threat by the Chinese in this speech before the American Bar Association, where he says "From a purely fiscal point of view, it also means
the Chinese are leveraging the American R&D budget — your tax dollars and mine — in support of their own war-fighting capability.")
Wolf also made reference to the April 10, 2008 BusinessWeek story: The New E-Espionage Threat, which is a must read for anyone dealing with these threats both in corporate America and the government.
His reference to Shane Harris' alarming cover story of the National Journal magazine, China's Cyber Militia brings up other issues though. Is this fact? or fiction? I've had a copy of the "Northeast Blackout Report" on my hard drive for years, and am very familiar with the incident from both open and classified conversations. This is the first time that I've seen the blackout blamed on the People's Liberation Army, and frankly, I'm skeptical. Harris says:
Rising to speak after Mr. Wolf, in support of his resolution, was US Representative Chris Smith (R-NJ), who used the opportunity to smear Google and Cisco, and call for support for his "Global Online Freedom" bill:
Like Wolf, Smith has reason to believe the attacks are sponsored by Beijing. He says:
My conclusion is that it is clear that China is developing Cyber espionage capabilities, and it is clear that there are many attacks using Chinese IP addresses, but I have not yet seen any hard evidence that Wolf's computer was definitely attacked by "the Chinese". Even Mr. Smith's accusation indicates that the HIR staff told him "it came through or from a Chinese IP address".
That's why I refused to jump on the Evil China Bandwagon when I was interviewed by IDG News's Robert McMillan for the story he called: Weak Evidence Links Congressmen's Cyber Attacks to China. The truth is that there are many active criminal enterprises hosting "bullet proof servers" in China, which are used by a wide range of cyber criminals for all sorts of attacks. It would simplify things if we could return to a Reaganesque view of the world where all evil comes from a single location, but it takes more evidence than I have seen so far to jump on this particular bandwagon. Certainly there is a great deal of state-sponsored hacking from China, but until the details of each particular investigation are known, we can't make statements with the degree of certainty that Congressman Smith would like.
The single line from his Resolution which has captured all of the attention came from this "Whereas" . . .
Whereas in subsequent meetings with HIR [The House Information Resources office] and officials from the Federal Bureau of Investigation, the outside source responsible for these incides was revealed to be located in the People's Republic of China;
More than 1100 news stories on Google mention the story, with some of the international mud-slinging using headlines like "US Accuses Chinese of Hacking Government Computers" which gained replies of "China says it's incapable of hacking Reps' computers".
Wolf didn't use such headlines -- the news story on his own website is headlined with Wolf Reveals House Computers Compromised by Outside Source. His office works with human rights activists and political dissidents around the world, and his emails and correspondence with some of these individuals was apparently compromised. He does say "My suspicion is that I was targeted by Chinese sources because of my long history of speaking out about China's abysmal human rights record." He also says that the Foreign Affairs Committee computers and that of other members who work "to help people who are suffering around the world" were similarly targeted.
That record is perhaps put most plainly in this impassioned speech by Representative Wolf from July 2007 -- Made in China, accuses China of poisoning toothpaste and toys, dumping products at below the cost of production on the international markets, arresting hundreds for religious beliefs and interring them in "slave labor camps", and compares their bid for the Olympics to that of the Nazis.
Wolf's words of warning on the Hill quote from several other sources as he issued his call for arms -- including a Congressional Research Service report indicating that 140 different foreign intelligence organizations regularly attempt to hack into the computer systems of US government agencies and US companies.
Joel Brenner, National Counterintelligence Executive of the Officer of the Director of National Intelligence used that figure in his speech here, and told CNN in October, it isn't just China, "there are about 140 foreign intelligence organizations trying to hack into the US government and US companies".
(Brenner also discussed the threat by the Chinese in this speech before the American Bar Association, where he says "From a purely fiscal point of view, it also means
the Chinese are leveraging the American R&D budget — your tax dollars and mine — in support of their own war-fighting capability.")
Wolf also made reference to the April 10, 2008 BusinessWeek story: The New E-Espionage Threat, which is a must read for anyone dealing with these threats both in corporate America and the government.
His reference to Shane Harris' alarming cover story of the National Journal magazine, China's Cyber Militia brings up other issues though. Is this fact? or fiction? I've had a copy of the "Northeast Blackout Report" on my hard drive for years, and am very familiar with the incident from both open and classified conversations. This is the first time that I've seen the blackout blamed on the People's Liberation Army, and frankly, I'm skeptical. Harris says:
One prominent expert told National Journal he believes that China’s People’s Liberation Army played a role in the power outages. Tim Bennett, the former president of the Cyber Security Industry Alliance, a leading trade group, said that U.S. intelligence officials have told him that the PLA in 2003 gained access to a network that controlled electric power systems serving the northeastern United States. The intelligence officials said that forensic analysis had confirmed the source, Bennett said. “They said that, with confidence, it had been traced back to the PLA.” These officials believe that the intrusion may have precipitated the largest blackout in North American history, which occurred in August of that year. A 9,300-square-mile area, touching Michigan, Ohio, New York, and parts of Canada, lost power; an estimated 50 million people were affected.
Rising to speak after Mr. Wolf, in support of his resolution, was US Representative Chris Smith (R-NJ), who used the opportunity to smear Google and Cisco, and call for support for his "Global Online Freedom" bill:
Google, for its part, has become the de facto center for China's ubiquitous anti-American, anti-Tibetan, anti-religious propaganda machine, while Cisco has made the dreaded Chinese secret police among the most effective in the world.
Like Wolf, Smith has reason to believe the attacks are sponsored by Beijing. He says:
The attackers hacked into files related to China. These contained legislative proposals directly related to Beijing, including the Global Online Freedom Act, e-mails with human rights groups regarding strategy, information on hearings on China--I chaired more than 25 hearings on human rights abuses in China--and the names of Chinese dissidents. While this absolutely doesn't prove that Beijing was behind the attack, it raises very serious concern that it was.
My conclusion is that it is clear that China is developing Cyber espionage capabilities, and it is clear that there are many attacks using Chinese IP addresses, but I have not yet seen any hard evidence that Wolf's computer was definitely attacked by "the Chinese". Even Mr. Smith's accusation indicates that the HIR staff told him "it came through or from a Chinese IP address".
That's why I refused to jump on the Evil China Bandwagon when I was interviewed by IDG News's Robert McMillan for the story he called: Weak Evidence Links Congressmen's Cyber Attacks to China. The truth is that there are many active criminal enterprises hosting "bullet proof servers" in China, which are used by a wide range of cyber criminals for all sorts of attacks. It would simplify things if we could return to a Reaganesque view of the world where all evil comes from a single location, but it takes more evidence than I have seen so far to jump on this particular bandwagon. Certainly there is a great deal of state-sponsored hacking from China, but until the details of each particular investigation are known, we can't make statements with the degree of certainty that Congressman Smith would like.
Friday, June 6, 2008
A Romantic June Storm
On June 2nd, starting at 5:53 PM, the UAB Spam Data Mine started receiving spam messages for the new version of the storm worm. The messages lead to a website titled "Who is loving you?" The "Love Riddles" web page invites you to "Just click here" to find out.
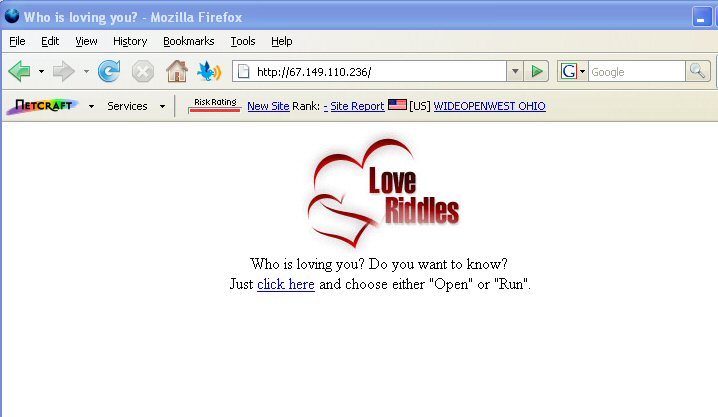
Its been four days since the new round of storm started up. How is the detection rate?
According to VirusTotal, only 6 of 32 AV engines are currently detecting this version of Storm:
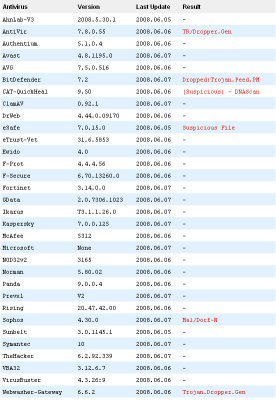
What should you be looking for?
So far we've seen these email subjects:
I belong to you
I Wanna Be With You
Just you and me
Missing you
Missing you with every breath
My heart beats just for you
My heart was stolen
Nothing's Gonna Change My Love For You
Stand by my side
Together forever
We belong together
You are my world
You are the ONE
You make my world beautiful
You make my world special
Which contained a single phrase of text, followed by an IP address. Here are the Text lines in the body of the message:
Always on my mind
Can't stay away from you
Crazy in love with you
Dreaming 'bout you
Here in my heart
I want to be with you
I'll Still Love You More
In your arms
Just you and me
Lonely without you
Lost In Your Eyes
Lucky to have you
Missing you
Not the same without you
Somebody loves you
Stand by my side
Together forever
Wanna kiss you
We belong together
You are always on my mind
You are my world
You feel up my senses
You have touched my heart
You make my world special
And here are a list of some of the IP addresses we've seen advertised in the messages:
24.232.184.4
59.54.57.99
60.43.108.150
61.93.161.182
62.117.121.10
67.149.110.236 (*)
68.74.124.34
69.137.21.212 (*)
77.87.88.101
78.185.150.204
83.4.43.26
85.121.85.185
86.126.123.109
86.126.169.39
116.111.209.201
116.72.162.240
121.152.86.118
123.201.37.59
124.107.138.98
151.49.127.7
190.172.212.240
190.18.188.183
190.53.11.211
190.55.159.93
200.115.109.46
200.125.111.190
200.74.9.216
200.8.248.229
201.209.64.220
201.250.43.228
203.223.246.131 (*)
222.105.121.8
At this time, only 3 of these IPs, marked with an (*) actually delivered the malware.

Its been four days since the new round of storm started up. How is the detection rate?
According to VirusTotal, only 6 of 32 AV engines are currently detecting this version of Storm:

What should you be looking for?
So far we've seen these email subjects:
I belong to you
I Wanna Be With You
Just you and me
Missing you
Missing you with every breath
My heart beats just for you
My heart was stolen
Nothing's Gonna Change My Love For You
Stand by my side
Together forever
We belong together
You are my world
You are the ONE
You make my world beautiful
You make my world special
Which contained a single phrase of text, followed by an IP address. Here are the Text lines in the body of the message:
Always on my mind
Can't stay away from you
Crazy in love with you
Dreaming 'bout you
Here in my heart
I want to be with you
I'll Still Love You More
In your arms
Just you and me
Lonely without you
Lost In Your Eyes
Lucky to have you
Missing you
Not the same without you
Somebody loves you
Stand by my side
Together forever
Wanna kiss you
We belong together
You are always on my mind
You are my world
You feel up my senses
You have touched my heart
You make my world special
And here are a list of some of the IP addresses we've seen advertised in the messages:
24.232.184.4
59.54.57.99
60.43.108.150
61.93.161.182
62.117.121.10
67.149.110.236 (*)
68.74.124.34
69.137.21.212 (*)
77.87.88.101
78.185.150.204
83.4.43.26
85.121.85.185
86.126.123.109
86.126.169.39
116.111.209.201
116.72.162.240
121.152.86.118
123.201.37.59
124.107.138.98
151.49.127.7
190.172.212.240
190.18.188.183
190.53.11.211
190.55.159.93
200.115.109.46
200.125.111.190
200.74.9.216
200.8.248.229
201.209.64.220
201.250.43.228
203.223.246.131 (*)
222.105.121.8
At this time, only 3 of these IPs, marked with an (*) actually delivered the malware.
Subscribe to:
Comments (Atom)