Appropriate folks have all the details, but I wanted to talk today about the infection technique being used by one of the 46 domains, http://entireall.info/.
The way the PHP code on the website works, whatever you are sent on the command line becomes the name of an ".exe" file that is available for download.
So, if you have been sent a spam, or a messagebook-comment-spam to get the new version of Adobe Flash Version 11, then the site will obligingly give you a file called "Adobe_Flash_v11.exe"
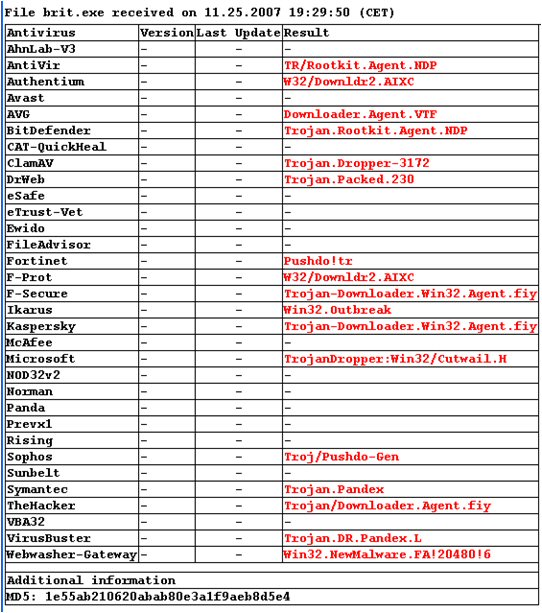
As of this timestamp, the root directory of this site is advertising itself as an "Adobe_Flash_v11.exe" updater. VirusTotal.com indicates that only 21% of its 32 anti-virus checks detect this as a virus.
Which brings me to the real topic of today's blog: Constantly Repacked Malware
If you had a link though for "Gar_New_Virus", such as:
(badsite here)/search.php?qq=Gar_New_Virus
Then that would be the name of the file it would offer to download, sticking a ".exe" on the end of it for you.
This site functions in a similar way to other malware sites, typically related to pornographic movie spam, such as "ThisFreeMovies.com", which will send you to download "VideoAccessCodecInstall" because you are lacking the proper Windows Media Player Codec to view a movie. The malware site will obligingly announce that it is the update site for VideoAccessCodecInstall and have a file VideoAccessCodecInstall.exe for you to download.
This latter file is currently undetectable by 21 of the 32 anti-virus products at Virus-Total, including no detection from F-Prot, Kaspersky, McAfee, and Symantec.
Those that do detect it, place it in a family called "Zlob" or "Zlobar".
These sites have been live for several months. Why do the major anti-virus products not detect their malware? It has to do with the fact that they are constantly "re-packing" the offensive code so that traditional signature-based anti-virus products are constantly playing catch up.
On the older of the two malware samples I downloaded just now, the detections identify ZLob:
- AntiVir = DR/Zlob.Gen
- AVG = Downloader.Zlob
- CAT-Quickheal = TrojanDownloader.Zlob.gen
- ClamAV = Trojan.Dropper-2557
- F-Secure = W32/Zlob.ARDM
- Microsoft = TrojanDownloader:Win32/Zlob.AMM
- Norman = W32/Zlob.ARDM
- Rising = Trojan.DL.Win32.Zlob.def
- Sophos = Troj/Zlobar-Fam
- TheHacker = Trojan/Downloader.gen
- Webwasher-Gateway = Trojan.Dropper.Zlob.Gen
- The other 21 products detect nothing.
But look what happens on the nearly identical virus which was packed more recently!
- AntiVir = TR/Crypt.XPACK.GEn
- Authentium = could be infected with an unknown virus
- AVG = Downloader.Zlob.NP
- eSafe = suspicious Trojan/Worm
- F-Prot = W32/Heuristic-119!Eldorado
- NOD32v2 = probably unknown NewHeur_PE virus
- Webwasher-Gateway = Trojan.Crypt.XPACK.Gen
- The other 25 products detect nothing.
We need to develop new methods for anti-virus products to deal more appropriately with "repacked" malware. Congratulations to those that are using Heuristic detection, or marking the file as suspicious because of the strange packing, but we need to know that these things are bad and warn the users!


 is scheduled to be sentenced on November 13th.
is scheduled to be sentenced on November 13th.
